- Program To Open Encrypted Channels Without
- Program To Open Encrypted Channels
- Program To Open Encrypted Channels Online
- Program To Open Encrypted Channels Using
Yes, you can unlock scrambled paid channels of satellites like Dish TV on Nss6, Hotbird, Nilesat, Eutelsat, Astra, HellasSat etc. You can unlock all premium paid HD & SD channels through Cccam Servers Cline method free of cost or in minimum cost. Just follow the tutorial below to unlock scrambled or $ sign channels. Only 5 apps made it to the list for military grade unhackable End-to-end encryption, data encrypted end-to-end is the only case where you can trust the service to protect your data. These apps are God sent for those in the opposition party in a country but can be badly abused by drug dealers, kidnappers, terrorists and more. Biss keys protected channels most of the time are capable of broadcast premium programs such as live sports globally, movies including TV series and so on. An example that comes to mind is the “ still blazing sports24 HD alternative ” Top open this feed package, you either need to get your hands on the active biss keys or get an auto roll. This is a list of free and open-source software packages, computer software licensed under free software licenses and open-source licenses.Software that fits the Free Software Definition may be more appropriately called free software; the GNU project in particular objects to their works being referred to as open-source. Infact there are thousand of channels on strong decoders which have been Encrypted dollar $ symbol.A common question that has been occurring,my blog readers always ask,how to watch (porn),Tv3 etc.On strong decoders.All these and other channel are there for you to watch.I have laid my hand on codes to Un-encrypted all these channel.while,i shall specifying some strong decoders which support.
Milestone recommends that you use a VPN for communication channels for installations where servers are distributed across untrusted networks. This is to prevent attackers from intercepting communications between the servers. Even for trusted networks, Milestone recommends that you use HTTPS for configuration of cameras and other system components.
Learn more
The following control(s) provide additional guidance:

Program To Open Encrypted Channels Without
- NIST 800-53 AC-4 Information Flow Enforcement
- NIST 800-53 AC-17 Remote Access
Program To Open Encrypted Channels
Was this article helpful?
Thanks for your feedback!
How does it work?
Matrix is really a decentralised conversation store rather than a messaging protocol. When you send a message in Matrix, it is replicated over all the servers whose users are participating in a given conversation - similarly to how commits are replicated between Git repositories. There is no single point of control or failure in a Matrix conversation which spans multiple servers: the act of communication with someone elsewhere in Matrix shares ownership of the conversation equally with them. Even if your server goes offline, the conversation can continue uninterrupted elsewhere until it returns.
This means that every server has total self-sovereignty over its users data - and anyone can choose or run their own server and participate in the wider Matrix network. This is how Matrix democratises control over communication.
By default, Matrix uses simple HTTPS+JSON APIs as its baseline transport, but also embraces more sophisticated transports such as WebSockets or ultra-low-bandwidth Matrix via CoAP+Noise.
The clients are all participating in the same Matrix room, which is synchronised across the three participating servers.
The server then signs the JSON including the signatures of the parent objects to calculate a tamper-resistent signature for the history.
 The destination servers perform a series of checks on the message:
The destination servers perform a series of checks on the message:- Validate the message signature to protect against tampering with history
- Validate the HTTP request's auth signature to protect against identity spoofing
- Validate whether Alice's historical permissions allow her to send this particular message
Program To Open Encrypted Channels Online
Alice, Bob and Charlie's homeservers all have different views of the message history at this point - but Matrix is designed to handle this inconsistency.
At this point Alice and Bob are in sync, but Charlie's room history has split - both messages 2 and 3 follow on from message 1. This is not a problem; Charlie's client will be told about Bob's message and can handle it however it chooses.
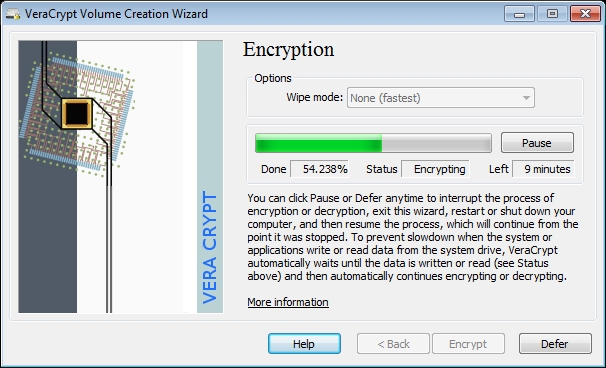
This effectively merges the split in history and asserts the integrity of the room (or at least her view of it).